TL;DR – Don’t buy it. It’s recommended that you use another CDN if you need Cloudflare’s ACM functionality, like second-level subdomains. But please read the final part of this post.
I’ve recently tried out Cloudflare’s Advanced Certificate Manager for my domain lumito.net, so since it is a service offered by a well-known company but didn’t get any independent reviews, today I’m going to make an in-depth one.
First of all, Cloudflare says (source: developers.cloudflare.com):
Advanced certificates
Advanced certificates offers a flexible and customizable way to issue and manage certificates.
Use advanced certificates when you want something more customizable than Universal SSL but still want the convenience of SSL certificate issuance and renewal.
Features
· Include the zone apex and less than 50 hosts as covered hostnames.
· Cover more than one level of subdomain.
· Select the preferred validation method (HTTP, TXT, or Email).
· Choose the certificate validity period (14, 30, 90, or 365 days).
· Choose the Certificate Authority to issue the certificate.
· Remove Cloudflare branding that are normally present on Universal certificates.
· Select a custom trust store for origin authentication.
· Control cipher suites used for TLS.
Enterprise customers can also purchase a subscription for Advanced Certificate Manager, which allows them to add up to 100 edge certificates per zone.
Let’s start with the first sentence: everything is more customizable that Cloudflare’s Universal SSL, and it’s true, you’re allowed to create, delete, add custom hostnames and change the certification authority for your Cloudflare certificates.
But let’s continue with the features:
- Include the zone apex and less than 50 hosts as covered hostnames: Yes, but there’s a catch: you are FORCED to have your zone name as a hostname, usually as the common name (CN). And no, the API doesn’t allow you to do that. Why, Cloudflare?
- Cover more than one level of subdomain: It’s true, and it works fine. But why is it useful if you need to put yourdomain.tld as your CN to protect webaccess.mail.beta.yourdomain.tld?
- Select the preferred validation method (HTTP, TXT, or Email): HTTP (which is only available through the API) and Email are only available when issuing certificates from DigiCert (continue reading for more information). Other CAs will require the use of the TXT DV method which, in my opinion, is the best.
- Choose the certificate validity period (14, 30, 90, or 365 days): That’s great, but 365 days certificates are available only from DigiCert and Sectigo.
- Choose the Certificate Authority to issue the certificate: The web UI only allows you to choose from
DigiCert, Let’s Encrypt and Google Trust Services. Update: Cloudflare is deprecating their DigiCert CA. But if you use the API, you can also choose Sectigo. - Remove Cloudflare branding that are normally present on Universal certificates:
That only applies for “DigiCert” certificates CN: instead of appearingUpdate: Cloudflare does no longer include branding in their SSL certificates.sni.cloudflaressl.comas the CN, it will show your FQDN. The intermediate certificate references to cloudflare will remain, and the Organization (O) field of the certificate will still showCloudflare, Inc.. If you choose to use another CA, it won’t show any Cloudflare branding. - Select a custom trust store for origin authentication: Didn’t know what it means, but it allows you to upload a custom certificate set when you are using the Full (strict) SSL mode, so you can use a private CA or tell Cloudflare to use just a few publicly trusted CAs for securing the CF-Server part of the connection. Pretty cool.
- Control cipher suites used for TLS: Haven’t tried it, but this Cloudflare’s page explains it pretty well. Warning: only available through the API.
- Enterprise customers […] up to 100 edge certificates per zone: Why is this function not available for regular customers?
Let’s continue with some screenshots, because neither Cloudflare nor any community member has ever posted about this product’s UI (as far as I know):
- Cloudflare’s ACM certificate ordering UI:
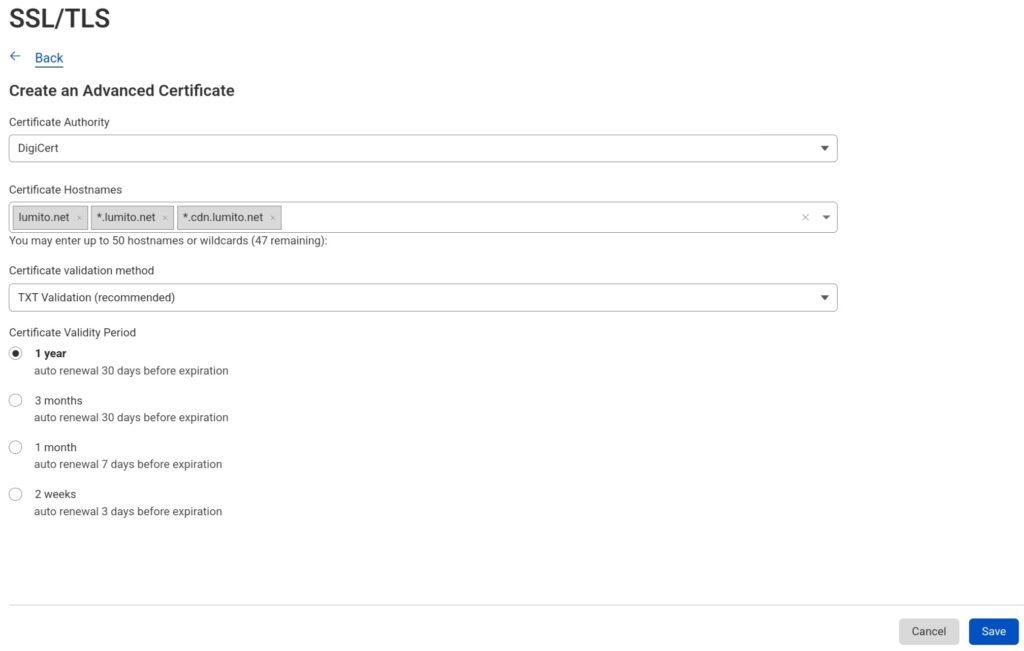
- SSL/TLS Edge certificates section with an Advanced certificate:
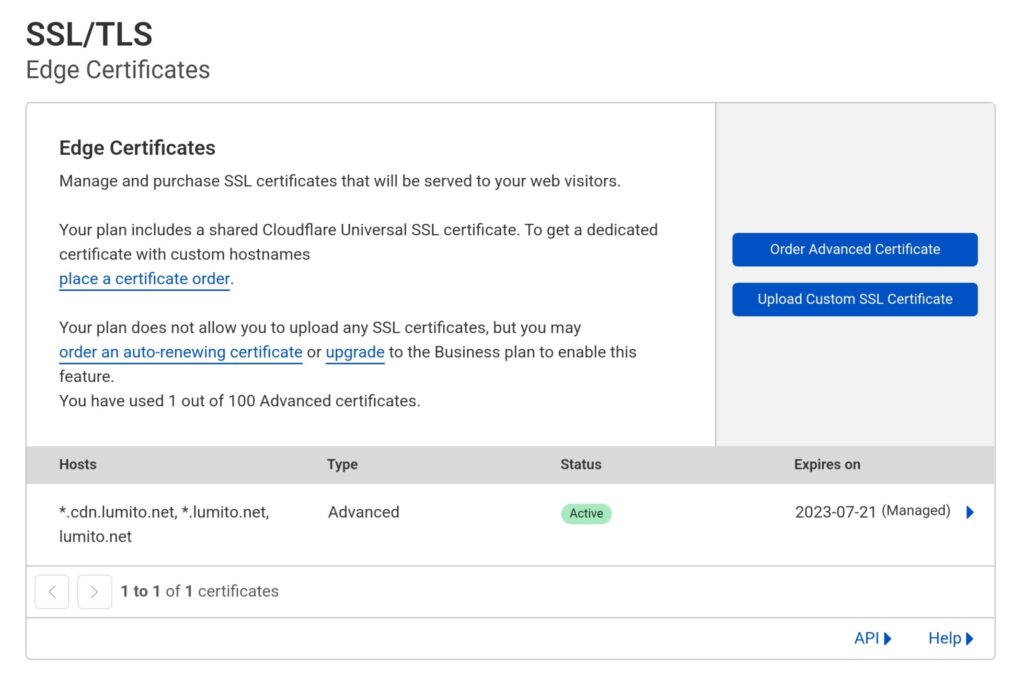
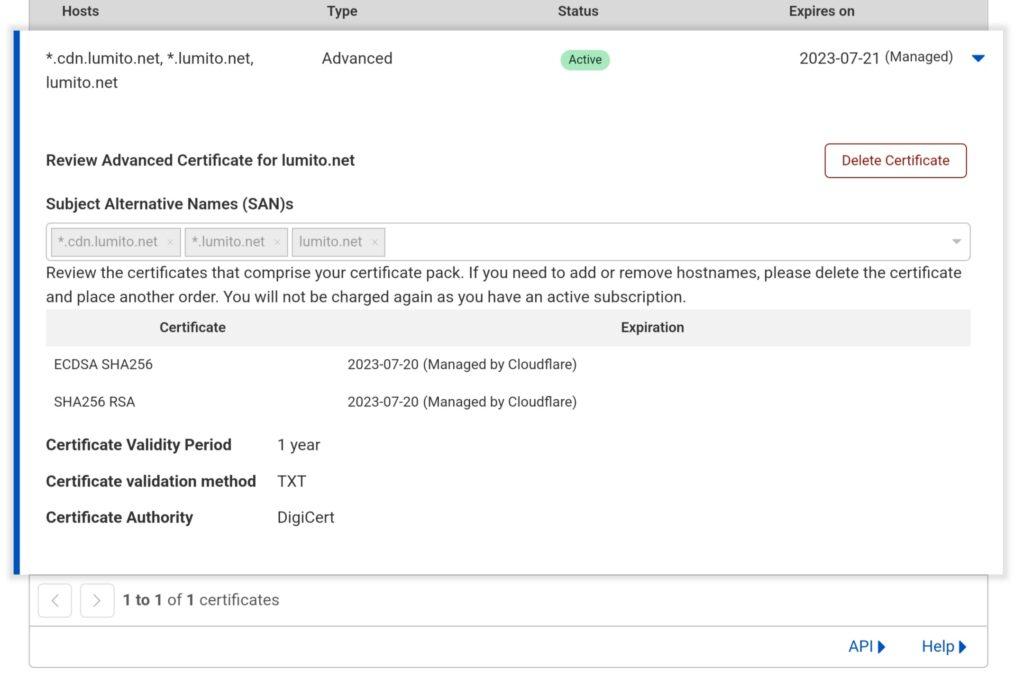
- Certificate in-detail view:
As you may have noticed, the interface is pretty lack in fuctionality, and far from being “advanced”. However, the API is much more powerful and allows you to do more things, as I commented in the “features” section above.
But, what’s the price? $10/month. You can get a good EV certificate for that price, not just DV.
However, this is far from over. Let’s look at the last point of this review: technical support.
A 10$/month paid plan does NOT include technical support via email, and you’ll need to use Cloudflare’s community forums for support. But after paying 10 bucks getting this reply when sending an email to support@cloudflare.com, treating you as a free user when you clearly aren’t:
Email support is not available for customers on your plan type. Upgrade now or you can still get great support for general questions and basic troubleshooting from our:
* Help center
* Developer documentation
* Cloudflare Community (staffed by Support Engineers)Code language: JavaScript (javascript)So, IMHO, don’t pay for this unless they include technical support.
Thanks a lot for reading the full review!
Update 1: I have finally been able to contact Cloudflare technical support, and they are helping me to solve my issue (ability to use a custom CN for DigiCert certificates and not include the zone name as a SAN). More information soon…
Update 2: I discovered that if you issue a certificate, it doesn’t get deleted after Cloudflare’s ACM subscription expiration. So you can just buy it once per year domain, generate a bunch of wildcard certificates and then discontinue the subscription for the rest of the year domain’s existance. Also, I’ve modified the rest of the post a bit.
Update 3: Updated the post with the new changes Cloudflare has made.